How to Avoid MFA Fatigue: Top Three Best MFA Practices
October 6, 2022
Recently, Uber experienced a cybersecurity incident and contacted law enforcement about the breach. An 18-year-old hacker took responsibility for the attack and listed a number of Uber databases and cloud services that they claimed to have breached. Although Uber states that there is no evidence of the incident involving access to sensitive user information (such as trip history), the attacker leaked screenshots indicating the company’s systems may have been severely compromised.
The attacker reportedly first gained access to Uber’s systems by targeting an individual employee and repeatedly sending them multi-factor authentication (MFA) login notifications. After over an hour, the attacker contacted the same target on WhatsApp pretending to be an Uber IT person and saying that the MFA notifications would stop once the target approved the login.
Sometimes known as “MFA fatigue”or “exhaustion attacks”, these incidents take advantage of authentication systems in which account owners merely have to approve a login through a push notification on their device instead of through other means, such as providing a randomly generated code.
In this blog, we will discuss in detail what MFA fatigue is and how security keys can help address such threats in the future.
What Is MFA Fatigue?
MFA fatigue is a social engineering technique. Also called an “MFA push spam”, this style of attack is growing more popular with threat actors as it does not require malware or phishing infrastructure and has proven to be incredibly successful.
When a company’s MFA is configured to use push notifications, an employee sees a prompt on their mobile device when somebody tries to log in with their credentials. These MFA push notifications ask the user to verify the login attempt and will show where the login is being attempted, as shown below.
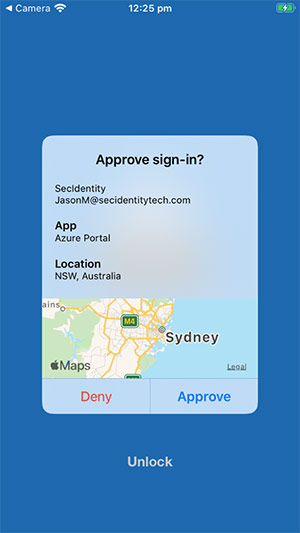
Source: Microsoft
An MFA fatigue attack occurs when a threat actor runs a script that attempts to log in with stolen credentials repeatedly. It causes what feels like an endless stream of MFA push requests to be sent to the account owner's mobile device. The goal is to keep this up, day and night, to break down the target's cybersecurity posture and inflict a sense of "fatigue" regarding these MFA prompts.
Often, such as in the case of Uber, the threat actors will push out repeated MFA notifications and then contact the target through email, messaging platforms, or over the phone, pretending to be IT support to convince the user to accept the MFA prompt. Eventually, the targets get so overwhelmed that they accidentally click on the “Approve” button or simply accept the MFA request to stop the inundation of notifications they were receiving on their phone.
MFA-prompt phishes have become more and more popular with attackers. In general, hackers have increasingly developed phishing attacks to work around two-factor authentication (2FA) as more companies deploy it. For instance, the recent Twilio breach demonstrated how horrible the consequences could be when a company that provides MFA services is itself compromised.
How Employees Can Tackle MFA Fatigue
If you are an employee who is the target of an MFA fatigue attack, and you receive a barrage of MFA push notifications, do not panic. Do not approve the MFA request, and do not talk to unidentified people claiming to be from your organization.
Instead, contact the known IT admins for your company, your IT department, or your supervisors and explain that you believe your account has been compromised and is under attack. If possible, you should also change the password for your account to prevent the hacker from continuing to log in and generate further MFA push notifications. Once your password has been changed, the threat actor will no longer be able to issue MFA spam, giving you and your admins room to breathe while the compromise is investigated.
Security experts also recommend disabling push notifications and simple “approve sign-in” requests. Instead, you should opt for a more secure method of numerical codes sent to your phone or an authentication app. On some systems, you can also limit the number of MFA requests that can be made. In other words, when a threshold is met, no additional notifications can be sent.
Of course, as this only works with stolen account credentials, the first line of defense is a strong, unique password. There is no better way to ensure you have one than a password manager. Using a strong password, along with an authenticator app and a configured MFA request threshold (if possible), is the safest way forward.
Top Three Best MFA Practices for Organizations
Here are three best practices that can help you ensure your MFA is robust against bypassing and hacking.
1. Deploy phishing-resistant MFA if possible
The U.S. government mandates all federal agencies to use “phishing-resistant” MFA. This means organizations must avoid any MFA technology that can easily be phished, such as one-time passcodes, SMS text messages, dynamic codes, and push notifications.
The strongest forms of MFA are based on the FIDO2 framework that allows users to unlock access to resources using fingerprint readers, cameras, and other device-level/hardware security checks on their devices. Since credentials do not leave a user’s device and are not stored anywhere, it eliminates the risk of phishing and credential theft.
2. Make existing phishable MFA solutions less phishable
There are several things organizations can do to make their current MFA less phishable. Most MFA solutions oversimplify (via simple allow/reject buttons) instead of displaying more context. Therefore, consider adding more information and context to user logins so that users can be more assured of what they are logging into. This can include things like device name, global ID, and device location. MFA solutions must also be tied to specific URLs, devices and hosts, so if a Man-in-the-middle (MitM) attack is involved, the solution will not allow access to the resource.
Moreover, ensure MFA is built using trusted cryptography. Additionally, an easy reset of credentials should not be allowed when MFA is not working. Instead, the recovery and bypass process must be rigorous. Finally, ensure that anything like a session cookie, security token, or seed value expires in less than 24 hours.
3. Improve security awareness around MFA
The core foundation of any security strategy is mitigating the root causes of threats. For instance, ransomware is not the problem. More troublesome is how the ransomware got into a system. Likewise, in the case of MFA attacks, phishing is the key root cause that needs to be addressed.
No matter how strong your MFA solution is, all stakeholders must understand the strengths and weaknesses of MFA and how hackers exploit users to bypass MFA defenses. Workers must be trained to identify and report unusual activity. They must especially be careful with push notifications and login attempts with which they are not directly involved. They should also use unique, 20-character passwords to avoid credential theft.
Always choose a defense-in-depth approach. Remove the risks associated with standard MFA by deploying one based on FIDO2. Ensure employees are awareness-trained to identify a cyberthreat masked as an MFA request. The deployment of FIDO2 eliminates the risk of phishing attacks, but ensuring users are well trained to identify cyberthreats is just as important.
The Ultimate Solution: FIDO2 Security Keys
Organizations that require physical authentication hardware keys for logins are successful in shielding themselves against such remote social engineering attacks. To safeguard against MFA fatigue, you need to use the highest assurance level for strong authentication.
As mentioned, the strongest forms of MFAs are based on FIDO2 standards and use cryptographic keys to emphasize strong authentication. Identiv's uTrust FIDO2 NFC+ Security Keys provide authentication to Windows 10 on standalone devices. The solution makes passwordless logins simple and secure. All you have to do is insert the device, tap the button on the key, and get secure access.
uTrust FIDO2 NFC+ Security Keys are FIDO Alliance-certified and TAA-compliant. The cryptographic security model of the devices eliminates the risk of phishing, password theft, and replay attacks. The FIDO cryptographic keys are stored on-device and are unique for each website, meaning they cannot be used to track users across sites.

Eliminate the risk of data breaches, phishing, password theft, and replay attacks with hardened MFA cybersecurity. uTrust FIDO2 NFC+ Security Keys replace passwords with a secure, fast, scalable, cost-effective login solution.
- Built for individuals, businesses, government agencies and contractors
- Eliminate the need to type and remember easily compromised passwords
- Connect to everyday devices, including phones, tablets, laptops, and desktops
- Pair with uTrust Key Manager Software and authenticate via Windows 10
- Works across all services (e.g., Gmail, Facebook, Salesforce, LinkedIn, etc.)
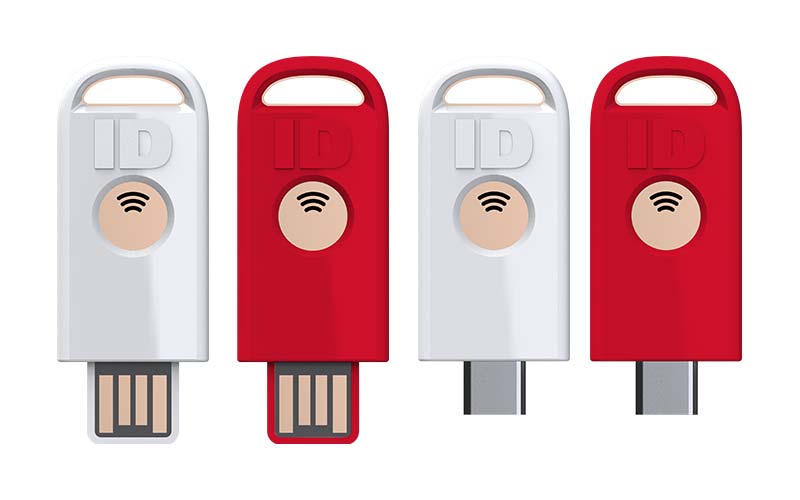
uTrust FIDO2 NFC+ Security Keys are available in two form factors: USB-A and USB-C. Both models feature near-field communication (NFC) functionality for contactless sign-on to applications. They provide multi-protocol support for FIDO2, FIDO U2F, PIV, TOTP, HOTP, and WebAuth enables strong MFA and removes the need for passwords. uTrust FIDO2 NFC+Security Keys are compatible with Windows, Linux, macOS, Android, and iOS, and are assembled in the US. Get in touch to request a demo.